By Minpeng Qi, Rajavelsamy Rajadurai, WG SA3 Vice Chairs and Suresh Nair, WG SA3 Chair
First published May 2023, in Highlights Issue 06
Release 18 is the first release for 5G-Advanced systems and a big step forward in security and privacy aspects of specifications, with 3GPP SA WG3 making progress on the enhancements in five key areas:
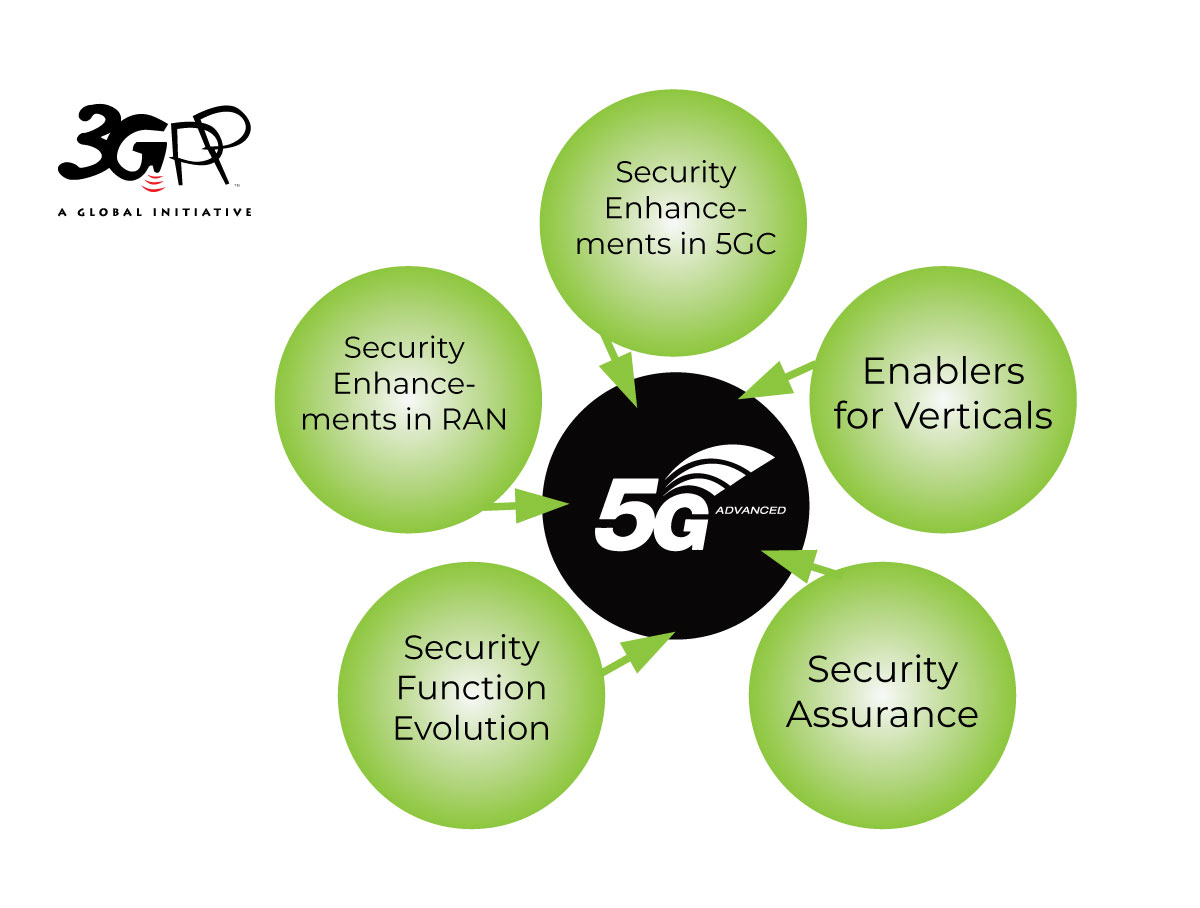
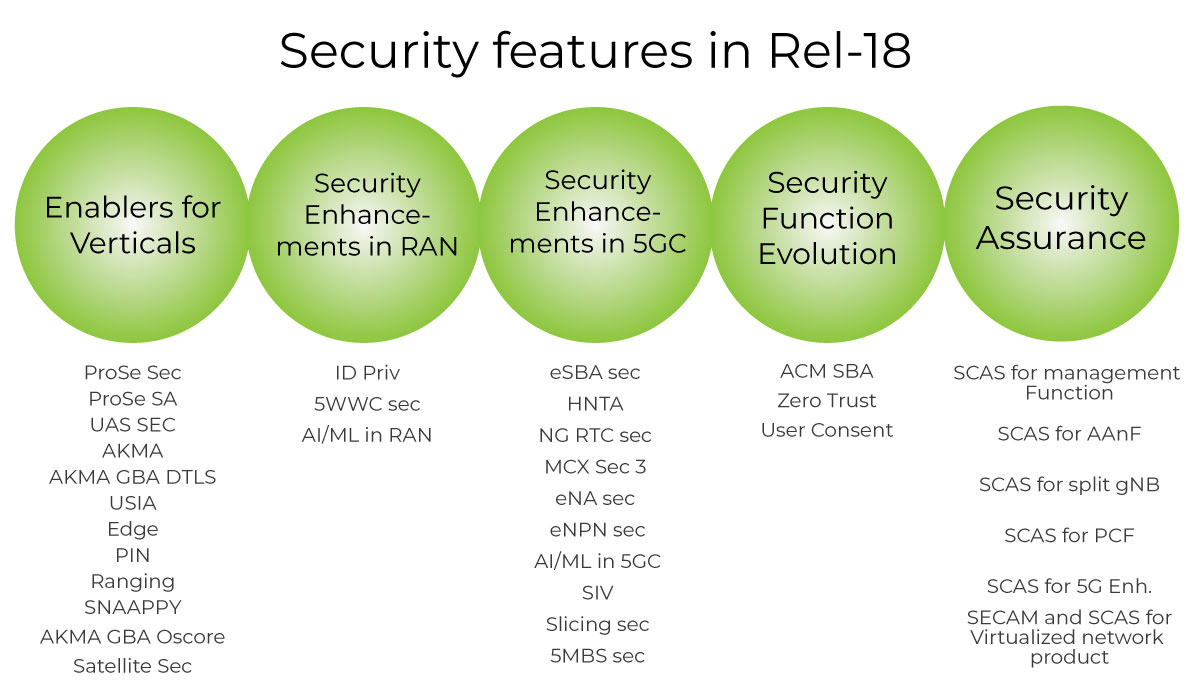
Security Enablers for Verticals
In Rel-18 the objective for Phase 2 of Proximity based services security is to specify security for UE-to-UE based relay Proximity Services, secondary authentication for remote UE connected through UE-to-Network Relay and security for path switching. For Authentication and Key Management for Applications (AKMA), Rel-18 adds roaming support. A further two work items are in progress to specify on how to use the AKMA / Generic Bootstrapping Architecture (GBA) to bootstrap the security context of IETF DTLS or OSCORE.
On Mission critical services, WG SA3 is specifying the security architecture for the WG SA6 specified new mission critical features like discreet listening and logging, temporary user identities, off network enhancements (such as ProSe) and so on.
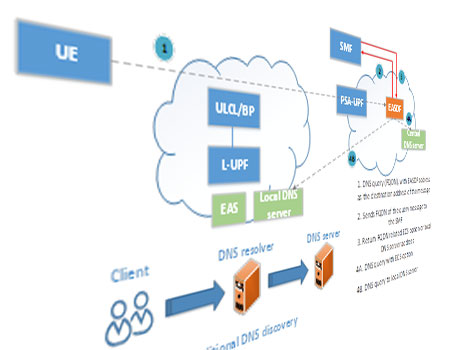
The EDGE computing framework is a promising new feature for which 3GPP built a foundation in Rel-17, in phase 2 (Rel-18), EDGE security features such as: privacy of new parameters exposed by UPF to AF, authentication mechanism negotiation and selection between Edge Enabler Client (EEC) and Edge Configuration Server/Edge Enabler Server (ECS/EES), authentication and authorization between Application Client and EEC and transport security for EDGE-9 and EDGE-10 interfaces are introduced.
Personal IoT Network (PIN), security aspects such as PIN Element authentication and authorization with 5G Core, security protection and access control protection for communications between PIN Elements, e.g. via PEGC or via 5GC, or for communications between PIN Elements and PEGC are added in Rel-18.
Subscriber-aware northbound API access in CAPIF (SNAAPPY) introduces “resource owner”, e.g. subscriber or user, as an entity capable of granting access to a protected resource and expands the CAPIF API Invoker to include UE applications. New security requirements related to API invocation, support for obtaining authorization from the resource owner and revocation of authorization by resource owner are considered to address in Rel-18.
Security Enhancement in 5G Core Network
Service Based Architecture (SBA), as the most important and outstanding feature designed for 5G networks, is also a big challenge for its security design. Currently SBA security discussions focus on security requirements on the SBA TLS certificate, on correction of the Oauth subscribe-notification case, and security clarification on NF consumer registration, etc.
Another feature - Security Impact on Virtualization is aimed to extend the 3GPP security capabilities which are required to provide direct explicit security visibility of the underlying virtualized infrastructure platform at the 3GPP layer and extensions to 3GPP functions to make use of such capabilities.
Home Network Triggered Authentication specifies which network function in the Home Network is better suitable to trigger the primary authentication and corresponding procedures as well as the potential impacts on the serving network, home network and the existing procedures.
In security aspects of Enablers for Network Automation (eNA) for 5G phase 3, security aspects of potential architecture enhancement on roaming, supporting federated learning, interaction between NWDAF and MDAS/MDAF are addressed. Further handling of sensitive information inherent to application detection, roaming and location information by NWDAF further enhances the security aspects for eNA.
In network slicing phase 3, the main objective is to specify the security procedure to support the HPLMN to provide roaming UE with the VPLMN slice information, enhanced authorization procedures for a UE to access network slices which support temporary slices, slice service areas mismatched with Tracking Area (TA) boundaries, and slices where S-NSSAI is not available in partial TAs of Routing Areas (RAs) and to support secured NSAC procedures to prevent DoS in the cases of NSAC for multiple service areas and network controlled UE behaviors.
In NG Realtime Communication security feature, support of existing service-based architecture in IMS media control interfaces and potential security aspects to support Data Channel usage in IMS network are specified.
Security assurance (for physical and virtualized network products)
Complementing 3GPP specifications for network architecture and services, to ensure the compliance of these specifications in network and system implementations of network and systems security, assurance certifications have been introduced by industry bodies such as GSMA. 3GPP SA3 has been developing test cases for these certifications.
Working Group SA3 has also started interacting with the European Union Agency for Cybersecurity (ENISA EU5G WGs) as they start to provide technical guidance on the security requirements in existing 5G standards and any additional requirements for future certification schemes.
Rel-18 introduces enhancements for all generic 5G SCAS specification, and introduces SCAS for specific network function such as AAnF, PCF and MnF. It defines security requirements and test cases for technical baseline, hardening and basic vulnerability test.
In another aspect, as 5G NFs are getting deployed as virtualized network functions, the gaps between virtualized implementation and physical implementation need to be considered. The SCAS specification for virtualized network product (TS 33.527) covers the specific security requirements for virtualized nodes.
Security Function Evolution
The Certificate management study looks at how to standardize the use of a single automated certificate management protocol and procedures for certificate life cycle events within intra-PLMN 5G SBA (i.e. to be used by all 5GC NFs including NRF, SCP, SEPP etc.), study the impact of service mesh in certificate management within 5G SBA, certificate lifecycle events like enrolment, renewal, revocation (e.g., OCSP, CRLs), status monitoring of a certificate and relation between certificate management lifecycle and NF management lifecycle.
Security Enhancement in RAN
There are a few features being introduced for security enhancements in the access stratum.
Privacy of identifiers over radio access (TR 33.870) is a comprehensive investigation of various 3GPP identifiers (e.g., user, subscriber, access network, core network, etc.), their privacy requirements, potential privacy threats and remediation.
Wireless Wireline Convergence phase2 (TR 33.887) addresses whether and how to identify, authenticate and authorize the Authenticable Non-3GPP devices and 3GPP devices (i.e. UE or N5CW devices) behind the Residential Gateway (RG) connecting to the network. Security aspects of supporting network slice in 5WWC and UE TNAP mobility in the 5GS are also part of this study.
In the RAN AI/ML study (TR 33.877) security aspects of employing AI/ML techniques in RAN are studied, with focus on the applicability of existing security mechanisms and whether any user privacy issues exist for the selected use cases in the related RAN group studies, without changing the current system design.
In Non public Networks (NPN) phase2 objectives are to support enhanced mobility by enabling support for idle and connected mode mobility between SNPNs without new network selection, support for non-3GPP access for SNPN, address new 3GPP WG SA1 requirements (e.g. TS 22.261 requirements from PALS work) related to NPN.
Uncrewed Aerial Systems (UAS) phase2 feature enhances security and addresses privacy threats. It looks at the corresponding security requirements that derive from the new architecture enhancements; in particular transport Broadcast Remote Identification and C2 communications via the 3GPP system or support aviation applications such as Detect And Avoid (DAA).
Another feature introduces mechanisms to securely identify the application for which the UE route selection policy (URSP) rule should be applied. The security and privacy issues specific to Ranging based services and sidelink positioning are also enhanced in another feature.
A feature on Zero Trust Analyses the 3GPP 5GS security scenarios related to the 5G core network that may benefit from a Zero Trust principle and identifies the associated threats.
Another feature ensures User Consent for 3GPP services to comply with user privacy choices.
MBS Phase2 features ensures security for UE's receiving Multicast MBS Session data in RRC Inactive state and efficient resource utilization for the same broadcast content to be provided to 5G Multiple Operator Core Network (MOCN) sharing scenarios.
The Enhanced SBA feature enables end to end authentication in roaming case if no cross-certification between operators is enabled, NF Service Consumer authentication of NRF and the NF Service Producer, impact of different deployment scenarios including the several SCPs, Verification of URI in subscription/notification, Dynamic authorization between SCPs or NF and SCP, End-to-End Critical HTTP headers/body parts integrity protection and Security of NRF service management.
In the NTN satellite access feature, enhanced security supporting discontinuous coverage with satellite access is provided.
In SA3 Rel-18 studies and normative works are now in progress and expected to be complete by September 2023.
Further Reading
- Specification Group page for 3GPP TSG SA WG3 - Security and Privacy
- Details of the features, acronyms and projects listed above - In the 3GPP Work Plan
- Article: Network Slicing Security for 5G and 5G Advanced Systems
- Article: Authentication and Key Management for Applications (AKMA) in 5G

 Technology
Technology