By Suresh Nair, 3GPP Working Group SA3 Chair, Saurabh Khare & Jing Ping (Nokia)
Published in Oct 2022, in Highlights Issue 05
3GPP have introduced many novel security features in 5G. These security features address the need to enhance the existing 4G security in different domains, such as access stratum (AS) between the UE and the base station or the Non Access Stratum (NAS) between the UE and the AMF, secure the PLMN 5G Core interface involving multiple network Functions (NFs) which use a Service Based Architecture (SBA) interface or the end to end interface between the UE and the UDM. 3GPP also defined security procedures for new industry segments and vertical markets such as Network Slicing, Non Public Networks (NPN), inter PLMN roaming, etc. One of the new security features defined is ‘Authentication and Key Management for Applications (AKMA)’, to enable applications to leverage the authentication of the UE performed by the PLMN and to use it for further authentication and authorization by an application and to bootstrap the necessary application security keys to the UE.
A full description of the AKMA feature is not intended here. Only a short description of the feature and its unique benefits are briefly mentioned. A full technical specification is contained in 3GPP TS 33.535.
Primary Authentication of the UE and AKMA: When a UE registers with the PLMN for the first time, the network performs a primary authentication of the UE. Only after the successful primary authentication of the UE, the UE is authorized for additional network services. 3GPP has specified two protocols 5G-AKA and EAP-AKA’ for primary authentication, both of which can be executed over 3GPP access and non-3GPP access. In the primary authentication, the subscription credentials and the shared secret stored in the USIM of the UE and the same stored in the UDM/UDR of the operator network is verified. Please note that in 5G, unlike in earlier 3G and 4G, the subscription permanent identifier SUPI is encrypted and sent to the UDM/UDR as a concealed subscription permanent identifier (SUCI). At the end of a successful primary authentication, the UE is admitted to network and the connection is secured using the derived session keys. In 5G, a new security network function, Authentication Server Function (AUSF) has been introduced in the 5G core (5GC) to manage the UE authentication using the SUCI or the SUPI and to manage the root session key KAUSF. The AUSF stores the root session key KAUSF and further keys are derived from this key. The UE and network derive further keys from the KAUSF. The radio connection between the UE and the base station is secured using the derived access stratum (AS) keys and the connection between the UE and core network is secured using the derived non access stratum (NAS) keys. The availability of the key KAUSF at the AUSF and the UE, as a result of the successful primary authentication has become an advantage since this key could be used to generate further keys that could be bootstrapped to secure different applications. AKMA key hierarchy as specified in TS 33.535 is shown in figure-1.

From the key KAUSF, an AKMA specific key KAKMA is derived. To secure individual applications, an application specific key KAF is derived from the KAKMA.
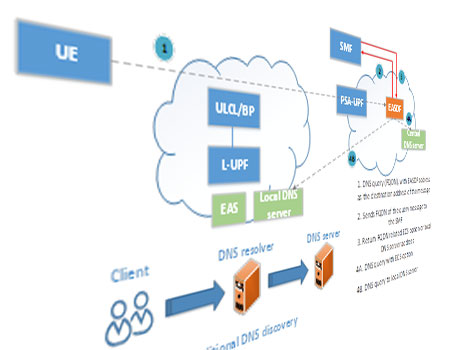
AKMA Architecture: In 4G, 3GPP defined the Generic Bootstrapping Architecture (GBA) in TS 33.220 to bootstrap keys to secure the application between the UE and an application server, after authenticating the UE using LTE-AKA protocol. A similar approach is taken in AKMA, but because of the 5G core service-based architecture, the AKMA architecture becomes entirely different compared to GBA.

A new logical entity, called the AKMA Anchor Function (AAnF) has been introduced to support the AKMA feature. From the KAUSF, the AUSF generates AKMA key KAKMA and sends it to the AKMA Anchor function AAnF. When UE tries to connect to an application server, the UE provides the AKMA temporary identifier to the application server. Based on this temporary identifier, the application server interacts with the AAnF to receive the specific session key KAF and UE identifier. The AF can use received session key KAF or further derive the keys based on the session key KAF to secure the communication between the UE and the application server. Thus AKMA provides a reliable framework for applications to authenticate the UE and secure the communication between the UE and the application server, leveraging the highly secure HPLMN based primary authentication. Please note, there is no separate authentication of the UE to support AKMA functionality. Instead, AKMA reuses the 5G primary authentication procedure for the sake of implicit authentication for AKMA services. Figure-2 above provides the architecture (a) where the Application Function (AF) is within the 5GC and part of the PLMN, whereas (b) provides the scenario where Application Function (AF) is outside the 5GC and the Application Function (AF) interacts with AKMA Anchor Function (AAnF) via the Network Exposure Function (NEF).
AKMA Procedures:
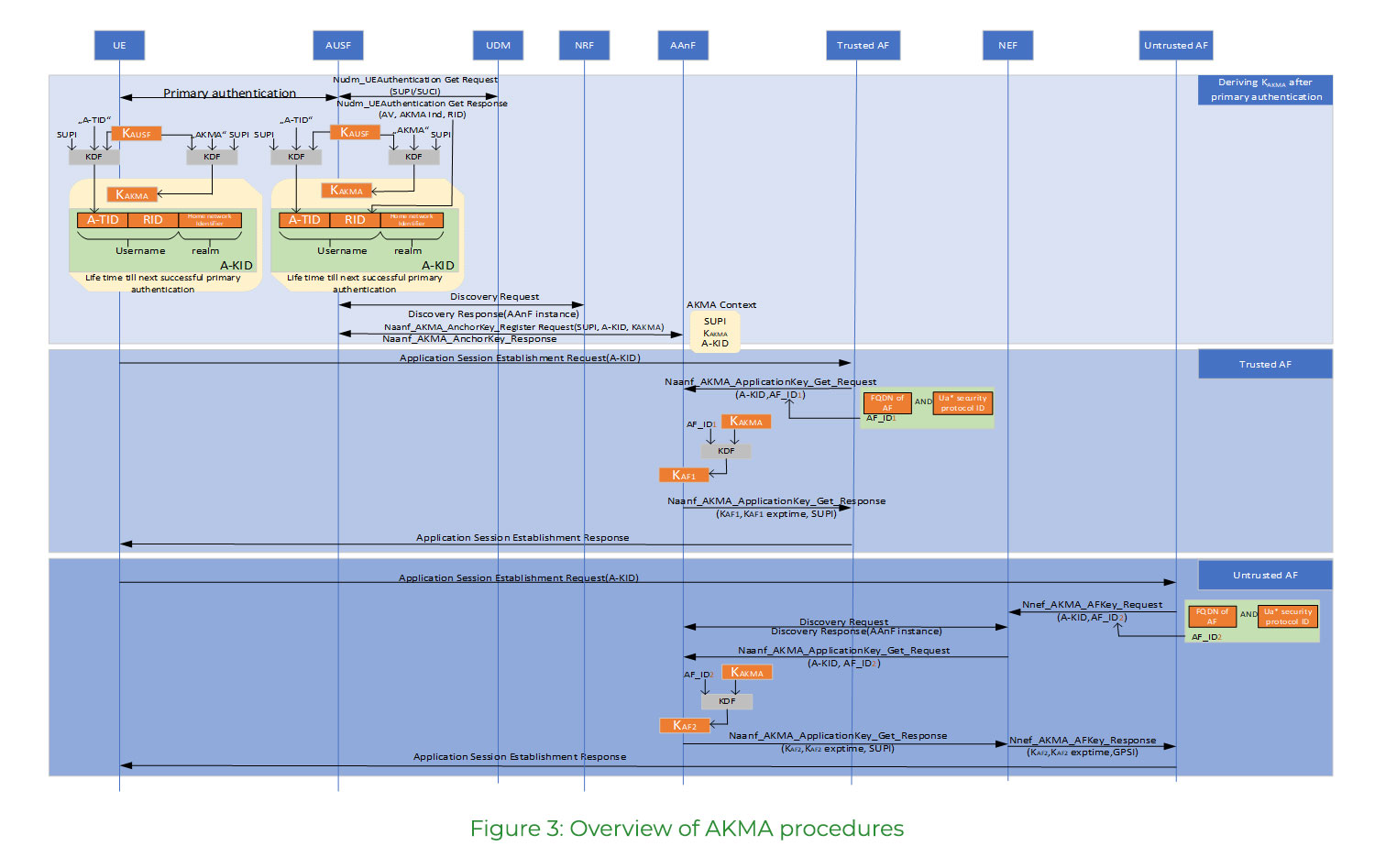
Figure 3: Overview of AKMA procedures, the following section provides a high-level view of the AKMA procedures. The stage1 shows that after the primary authentication of the UE, the AKMA key KAKMA is derived from the key KAUSF. Correspondingly, a AKMA Key ID A-KID is also generated at the UE and AUSF. The A-KID is also used as a temporary identifier for AKMA. The main SBA procedures between the AUSF, NRF and the AAnF are also shown, resulting in the creation of a UE context within the AAnF.
The second stage of the diagram shows how a trusted AF within the trusted PLMN core interacts with the AAnF and a key KAF is generated to secure the communication between the UE and the AF.
The third stage of the diagram shows how an untrusted AF outside the PLMN core interacts with the AAnF via the network exposure function NEF and a key KAF is generated to secure the communication between the UE and the AF.
Please note that the application specific protocol between the UE and the application function AF, Ua* is left unspecified in TS 33.535. Applications can develop this protocol specific to their needs.
AKMA advantages:
- Since the AKMA framework uses authentication and authorization of the UE leveraging the PLMN credentials stored on the USIM, this becomes as strong as the network primary authentication and subsequent keys derived further to UE and Application Function (AF) interface.
- The Application Functions can leverage the authentication service provided by the AKMA Anchor Function (AAnF) without additional CAPEX and OPEX.
- The architecture provides a direct interface between the UE and the AF where a customized application-specific interface can be built, including the key management, key lifetime extension, etc.
For more about 3GPP SA WG3 - Security and Privacy - go to: https://www.3gpp.org/3gpp-groups/service-system-aspects-sa/sa-wg3


 Technology
Technology